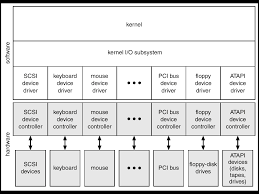
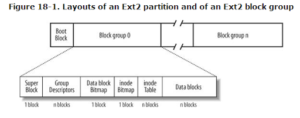
The running device is chargeable for numerous different components of disk management, too. Here we talk disk initialization, booting from disk, and horrific-block recovery.
Disk Formatting
A new magnetic disk is a clean slate: It is only a platter of a magnetic recording material. Before a disk can save facts, it should be divided into sectors that the disk controller can study and write. This manner is known as low-stage formatting, or bodily formatting. Low-stage formatting fills the disk with a unique facts shape for every zone. The facts shape for a zone commonly includes a header, a facts place (typically 512 bytes in length).
When the controller writes a zone of facts at some point of ordinary I/O, the ECC is up to date with a cost calculated from all of the bytes with inside the facts place. When the world is study, the ECC is recalculated and is as compared with the saved cost.
If the saved and calculated numbers are different, this mismatch suggests that the facts place of the world has turn out to be corrupted and that the disk zone can be horrific . The ECC is an error-correcting code as it includes sufficient records that, if only some bits or facts had been corrupted, the controller can become aware of which bits, have modified and may calculate what their accurate values ought to be. It then reviews a recoverable tender error. The controller routinely does the ECC processing on every occasion a zone is study or written.
Most difficult disks are low-stage-formatted on the manufacturing unit as part of the producing manner. This formatting permits the producer to check the disk and to initialize the mapping from logical block numbers to defect-unfastened sectors at the disk.
For many difficult disks, whilst the disk controller is informed to low-stage-layout the disk, it may additionally be instructed what number of bytes of facts area to go away among the header and trailer of all sectors.
Some running structures can deal with most effective a zone length of 512 bytes. To use a disk to keep files, the running device nonetheless wishes to document its personal facts systems at the disk. It does so in steps. The first step is to partition the disk into one or extra companies of cylinders.
The running device can deal with every partition as though it had been a separate disk. For instance, one partition can keep a duplicate of the running device’s executable code, even as any other holds person files. After partitioning, the second one step is logical formatting (or introduction of a report device).
In this step, the running device shops the preliminary report-device facts systems onto the disk. These facts systems may also encompass maps of unfastened and allotted area (a FAT or modes) and an preliminary empty directory.
To boom efficiency, maximum report structures organization blocks collectively into large chunks, regularly known as clusters. Disk I/O is finished thru blocks, however report device I /O is finished thru clusters, successfully assuring that I/O has extra sequential-get right of entry to and less random-get right of entry to characteristics.
Some running structures supply unique packages the capacity to apply a disk partition as a big sequential array of logical blocks, with none report-device facts systems. This array is every now and then known as the uncooked disk, and 1 /O to this array is named uncooked I/O. For example, a few database structures decide on uncooked I/O as it permits them to manipulate the precise disk vicinity in which every database document is saved.
Raw I/O bypasses all of the report-device offerings, which includes the buffer cache, report locking, prefetching, area allocation, report names, and directories. We can ensure programs extra green through letting them enforce their personal unique-reason garage offerings on a uncooked partition, however maximum programs carry out higher once they use the everyday report-device offerings.
Boot Block
For a laptop to begin jogging—for instance, whilst it’s miles powered up or rebooted—it should have an preliminary software to run. This preliminary bootstrap software has a tendency to be easy. It initializes all components of the device, from CPU registers to tool controllers and the contents of predominant memory, after which begins of evolved the running device.
To do its activity, the bootstrap software reveals the operating system kernel on disk, hundreds that kernel into memory, and jumps to an preliminary cope with to start the running-device execution. For maximum computers, the bootstrap is saved in study-most effective memory (ROM).
This vicinity is convenient, due to the fact ROM wishes no initialization and is at a set vicinity that the processor can begin executing whilst powered up or reset. And, given that ROM is study most effective, it can’t be inflamed through a laptop virus. The trouble is that converting this bootstrap code calls for converting the ROM, hardware chips. For this reason, maximum structures save a tiny bootstrap loader software with inside the boot ROM whose most effective activity is to herald a complete bootstrap software from disk. The complete bootstrap software may be modified easily: A new edition is surely written onto the disk. The complete bootstrap software is saved in ”the boot blocks” at a set vicinity at the disk. A disk that has a boot partition is known as a boot disk or device disk.
Disk Management
The code with inside the boot ROM instructs the disk controller to study the boot blocks into memory (no tool drivers are loaded at this point) after which begins of evolved executing that code. The complete bootstrap software is extra state-of-the-art than the bootstrap loader with inside the boot ROM; it can load the whole running device from a non-constant vicinity on disk and to begin the running device jogging. Even so, the entire bootstrap code can be small.
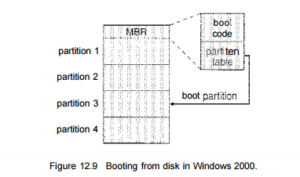
Let’s recall for example the boot manner in Windows 2000. The Windows 2000 device locations its boot code with inside the first zone at the difficult disk (which it phrases the grasp boot document, or MBR). Furthermore, Windows 2000 permits a difficult disk to be divided into one or extra walls; one partition, diagnosed because the boot partition, includes the running device and tool drivers.
Booting starts of evolved in a Windows 2000 device through jogging code this is resident with inside the device’s ROM memory. This code directs the device to study the boot code from, the MBR. In addition to containing boot code, the MBR includes a desk list the walls for the difficult disk and a flag indicating which partition the device is to be booted from.
Bad Blocks
Because disks have transferring elements and small tolerances (take into account that the disk head flies simply above the disk surface), they’re vulnerable to failure. Sometimes the failure is complete; on this case, the disk wishes to get replaced and its contents restored from backup media to the brand new disk. More regularly, one or extra sectors turn out to be faulty. Most disks even come from the manufacturing unit with horrific blocks.
Depending at the disk and controller in use, those blocks are treated in loads of ways. On easy disks, which includes a few disks with [DE controllers, horrific blocks are treated manually. For instance, the MS-DOS layout command plays logical formatting and, as part of the manner, scans the disk to discover horrific blocks. If layout reveals a horrific block, it writes a unique cost into the corresponding FAT access to inform the allocation exercises now no longer to apply that block.
More state-of-the-art disks, which includes the SCSI disks utilized in high-quit PCs and maximum workstations and servers, are smarter approximately horrific-block recovery. The controller continues a listing of horrific blocks at the disk. The listing is initialized at some point of the low-stage formatting on the manufacturing unit and is up to date over the lifestyles of the disk.
Low-stage formatting additionally units apart spare sectors now no longer seen to the running device. The controller may be instructed to update every horrific zone logically with one of the spare sectors. This scheme is referred to as zone sparing or forwarding.
A normal horrific-zone transaction is probably as follows: The running device attempts to study logical block 87. The controller calculates the ECC and reveals that the world is horrific. It reviews this locating to the running device.
The subsequent time the device is rebooted, a unique, command is administered to inform the SCSI controller to update the horrific zone with a spare. After that, on every occasion the device requests logical block 87, the request is translated into the substitute zone’s cope with through the controller.
Such a redirection through the controller may want to invalidate any optimization through the running device’s disk-scheduling algorithm! For this reason, maximum disks are formatted to offer some spare sectors in every, cylinder and a spare cylinder as well.